Detect hidden Windows processes with ease
Process Master is a lightweight process monitoring tool built to detect hidden or stealth processes in Windows environments. Designed by Backfaces Team, this utility offers a no-frills way to spot anomalies that standard tools like Task Manager might miss. It’s ideal for advanced users looking to hunt down rootkits, suspicious background tasks, or system intrusions on older machines.
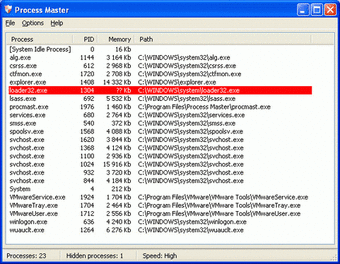
With its simple interface and low resource demand, Process Master provides quick visibility into running applications. It identifies each process by name, PID, memory usage, and path. Most importantly, it detects hidden processes, which are often symptoms of malware or cloaked executables. Red flags—like “?? Kb” memory usage—help users instantly spot suspicious entries.
Find the unseen and stay in control
Process Master keeps things simple by focusing on one job—uncovering hidden or stealthy processes that other tools might miss. It does this by comparing what Windows says is running to what’s actually in memory. If something’s trying to hide, like an old rootkit, Process Master can spot the mismatch. It’s a bit barebones, but if you know what you're looking for, it gets the job done.
The program is tiny, fast, and plays nicely with older systems like Windows XP or 2000. Its layout is plain—just a sortable table—but that’s all it really needs. You can terminate suspicious processes directly, but don’t expect fancy features like graphs, logs, or built-in malware scans. What you do get is a clean, distraction-free view of your system's guts.
Being from 2006, it’s not built for today’s threats. You won’t catch modern rootkits or sneaky zero-day malware here. But for vintage machines, system restorations, or malware forensics, it’s still handy. Back in the day, it was one of the few tools that could sniff out nasties like HackerDefender. It carved out a niche then—and for the right user, it still holds up.
A niche but powerful legacy tool
Process Master remains a useful utility for uncovering cloaked or hidden processes that evade standard Windows tools. Its low-level detection methods offer value for retro malware hunting, system diagnostics, or forensic analysis—particularly on legacy machines. While it lacks modern safeguards, its speed, clarity, and targeted scope make it a solid companion for experienced users when paired with up-to-date antivirus or anti-rootkit tools.